Cybersecurity Maturity Model Certification (CMMC):
What it is and what it means for the Defense Industrial Base
CMMC: HOW DID WE GET HERE?
Organizations that work with the Department of Defense (DoD), known as Defense Industrial Base (DIB), are now well aware of the cybersecurity mandates that have been sweeping across the defense industry over the past several years. In 2015, The U.S. Department of Defense published the Defense Acquisition Federal Regulation Supplement, known as DFARS, which mandates that private DoD Contractors adopt cybersecurity standards according to the NIST SP 800-171 cybersecurity framework. This is all part of a government-led effort to protect the U.S. defense supply chain from foreign and domestic cyber threats and reduce the overall security risk of the sector.
On January 31, 2020, the DoD announced the Cybersecurity Maturity Model Certification (CMMC). This new framework is to ensure their contractors and suppliers have appropriate cybersecurity frameworks in place to protect data such as Controlled Unclassified Information (CUI), Federal Contact Information (FCI), and other information. In September 2020, the DoD published an interim rule to the Defense Federal Acquisition Regulation Supplement (DFARS), which implemented the DoD’s initial vision for the CMMC program (“CMMC 1.0”) and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). This interim rule became effective on November 30, 2020, and was meant to phase in over the next five years.
However, in March 2021, prompted by over 850 public comments, the Department initiated an internal review of CMMC’s implementation. This comprehensive assessment urged the DoD to refine the policy and program. In November 2021, the Department announced “CMMC 2.0,” an updated program designed to achieve these primary goals:
- Safeguard sensitive information to enable and protect the warfighter
- Dynamically enhance DIB cybersecurity to meet evolving threats
- Ensure accountability while minimizing barriers to compliance with DoD requirements
- Contribute towards instilling a collaborative culture of cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
The rule enacting CMMC 2.0 finally became effective December 16, 2024.
The Federal Register summarized the final rule thusly:
With this final rule, DoD establishes the Cybersecurity Maturity Model Certification (CMMC) Program in order to verify contractors have implemented required security measures necessary to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). The mechanisms discussed in this rule will allow the Department to confirm a defense contractor or subcontractor has implemented the security requirements for a specified CMMC level and is maintaining that status (meaning level and assessment type) across the contract period of performance. This rule will be updated as needed, using the appropriate rulemaking process, to address evolving cybersecurity standards, requirements, threats, and other relevant changes.
https://www.federalregister.gov/d/2024-22905/p-3
Many DoD contractors and subcontractors will have to complete the CMMC assessment in order to service DoD contracts. Understanding the current state of your cybersecurity program and how it measures up against the CMMC framework is the critical first step in this process.
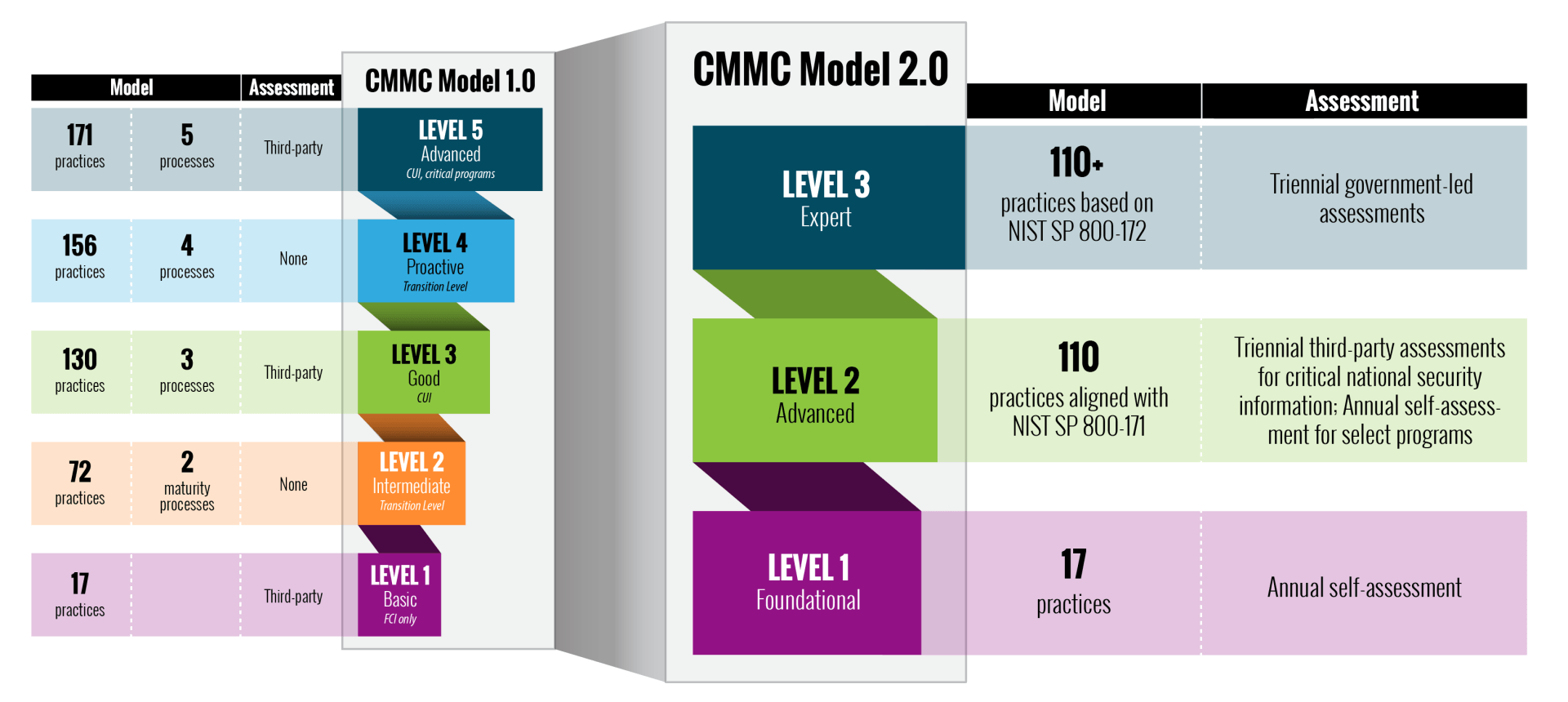
CMMC 1.0 > CMMC 2.0: WHAT CHANGED?
Reduction of Certification Levels
CMMC 2.0 reduces the framework from five certification levels to three. The levels were renamed to Level 1, Foundational (previously Level 1); Level 2, Advanced (previously Level 3); and Level 3, Expert (previously Level 5).
Self-Assessments and Government-Led Assessments
The most dramatic shift in CMMC 2.0 is removal of the requirement that all certification assessments be performed by third-party organizations, dubbed CMMC Third-Party Assessment Organizations (C3PAOs).
Under the updated framework, Level 1 certification and certain nonprioritized acquisitions assigned Level 2 will require only an annual self-assessment and accompanying contractor affirmation in the Supplier Performance Risk System (SPRS). Prioritized acquisitions assigned Level 2 will require a C3PAO assessment every three years. All certifications at Level 3 will require a government (rather than C3PAO) assessment every three years.
Limited POAMs
Under certain circumstances, CMMC 2.0 will allow contractors to implement time-limited Plans of Action and Milestones (POAMs) in order to achieve full certification. DoD will specify an absolute number of cybersecurity requirements that must be achieved prior to contract award, as well as a small set of critical requirements that must always be achieved prior to award and which may not appear in a contractor’s POAM. The allowance for a POAM, even if limited, is a significant change from the prior model, which required that contractors achieve the full applicable CMMC level certification to even be eligible to submit a proposal for any defense contracts.
Limited Waivers
Under certain limited circumstances for select mission critical acquisitions, CMMC 2.0 will allow contractors to obtain waivers of CMMC requirements. Waivers must be approved by DoD senior leadership and will be time-limited. Again, even with limitations, a CMMC waiver process is a large shift from the previous model, where certification was a “go/no-go” criterion for bidding on defense contracts.
Streamlined Practices
CMMC 2.0 draws only from the National Institute of Standards and Technology Special Publication (NIST SP) 800-171 and NIST SP 800-172 to create its cybersecurity standards. It no longer contains any cybersecurity practices drafted specifically for the CMMC framework or practices pulled from various domestic and international cybersecurity standards.
Removal of Maturity Processes
CMMC 1.0 proposed to evaluate both cybersecurity processes and cybersecurity practices. Practices evaluated technical activities required for certification, whereas processes evaluated the extent of institutionalization of those practices. CMMC 2.0 eliminates the concept of maturity processes and contains only the cybersecurity practices themselves.
CMMC 2.0: THE THREE LEVELS
Level 1: Basic Cyber Hygiene (Foundational)
This is the most basic level of certification and consists of several practices that correspond directly to essential safety conditions outlined in the Federal Acquisition Regulation (FAR).
Level One consists of 17 basic cybersecurity practices such as implementing Access Control as well as Identity and Authentication.
Other practices include:
- Asset Management (AM)
- Audit and Accountability (AA)
- Awareness and Training (AT)
- Configuration Management (CM)
- Incident Response (IR)
- Maintenance (MA)
- Media Protection (MP)
- Personnel Security (PS)
- Physical Protection (PP)
- Recovery (RE)
- Risk Management (RM)
- Security Assessment (SAS)
- Situational Awareness (SA)
- System and Communications Protections (SCP)
- System and Information Integrity (SII)
The primary aim is to protect federal contract information, and it is mandatory for anyone looking to obtain a DoD contract.
Level 2: Intermediate Cyber Hygiene (Advanced)
Level 2 requires recorded policies for each of the 17 practices covered by the certification and documentation for completing each practice's policies.
It is a more extensive set of security practices - 55 in addition to the 17 in Level 1 - that are a subset of the NIST SP 800-171 requirements, which protect controlled unclassified information in the IT of government contractors and subtractors.
The goal is to create a basic sense of cybersecurity for any organization that has Controlled Unclassified Information (CUI), which requires a higher level of security than an organization with only Federal Contact Information (FCI).
Level 3: Good Cyber Hygiene (Expert)
The final level mandates organizations establish and maintain a plan to implement the requirements of CMMC.
Level 3 includes all the practices included in Levels 1 and 2, the requirements stated in NIST SP 800-171 as well as NIST SP 800-172; and an additional 58 practices.
As a result of the alignment of CMMC to NIST standards, the Department’s requirements will continue to evolve as changes are made to the underlying NIST SP 800-171 and NIST SP 800-172 requirements.



